API Penetration Testing
What is API Penetration Testing?
Web application penetration testing services proactively assess applications to identify vulnerabilities, such as those that could lead to the loss of sensitive user and financial information. Web applications play a vital role in business success and are an attractive target for cybercriminals, so regular web app pen testing is essential.
Predicitive Intelligence is a CREST-certified web app pen testing company. Our expert team, which includes Certified Web Application Testers (CCT APP), are hugely experienced at performing web application penetration testing and website security testing and can help your organisation to identify and remediate a wide range of risks.

Modern apps need modern security
Web apps, whether cloud-based or on-premises, are potentially your most vulnerable assets. They’re constantly changing and highly accessible, and they often contain sensitive data, so you can’t rely on outdated, consulting-heavy pen tests to secure them. Instead, with Bugcrowd Web Application Pen Tests, you can improve your security posture by running highly configurable, high-impact tests at scale to shut those attack vectors down–with prioritized results and tester progress available 24/7 via a rich Pen Test Dashboard.
Find and fix common issues fast
Identify hidden vulns that involve human interaction such as business logic flaws, identity management bypasses, and misconfigurations.
Tackle complex apps with ease
Test complex apps and features for payment processing, purchasing, file uploads, and elaborate user workflows.
Rely on battle-tested standards
Our methodology follows common testing standards such as OWASP, The Web Application Hacker Handbook, and SANS Top 25.
Use the right pentesters and tools for the task
We combine human-driven testing by a curated team, the latest scanners, and custom tooling to get the high-impact results you want.
Vulnerabilities
Testing includes assessing applications for vulnerabilities listed in the OWASP Top 10, the Open Web Application Security Project's ten most critical application security risks. Our web application security testing team will help to identify vulnerabilities including: Injection flaws
Injection flaws
Sensitive Data Exposure can occur when a web application does not protect sensitive information, such as health records or PII.
Database interaction errors
Sensitive Data Exposure can occur when a web application does not protect sensitive information, such as health records or PII.
Authentication weaknesses
Misconfigurations in session management can lead to many attacks, such as session hijacking, fixation or unauthorised access.
Flaws in application logic
Misconfigurations in session management can lead to many attacks, such as session hijacking, fixation or unauthorised access.
Broken access controls
Using outdated components with known vulnerabilities can often expose a web app to various software-related attacks.
Input validation problems
Using outdated components with known vulnerabilities can often expose a web app to various software-related attacks.
Poor session management
Misconfigurations in session management can lead to many attacks, such as session hijacking, fixation or unauthorised access.
Security misconfigurations
Misconfigurations in session management can lead to many attacks, such as session hijacking, fixation or unauthorised access.
What does Website Security Testing include?
File Inclusion Vulnerabilities
Insufficient Transport Layer Security (TLS)
Cross-Site Request Forgery (CSRF)
Insecure Direct Object References (IDOR)
Session Hijacking
Insecure Deserialisation
Cross-Site Scripting
Directory Traversal
Command Injection
XML External Entities
SQL Injection
Path Traversal
Predicitive Intelligence’s web app pen testing experts work with you to define any websites and applications in scope and devise an appropriate testing strategy.
Our web application penetration testers use the latest intelligence gathering techniques to uncover security and technical information about the websites and applications in-scope.
Our web application penetration testers use their offensive security expertise and knowledge of the latest hacking tools to identify exploitable security vulnerabilities.
Once vulnerabilities have been identified, our pen testers develop and execute a plan to exploit them, but in a safe way that avoids damage and disruption.
Once a web application security test is complete, our testers document key findings and supply prioritised remediation guidance to help address any identified exposures.
What are the benefits of Web Application Penetration Testing?
Web app pen testing identifies the security gaps in your web applications, offering a path to remediation before attackers exploit them.
- Regulatory Compliance: Many industries, such as healthcare and finance, have strict data protection standards. Regular web application penetration testing helps maintain these standards.
- Cost Savings: A security breach can have devastating financial consequences. Penetration testing is a proactive measure that could save your business money in the long run.
- Protecting Brand Reputation: A security breach can damage your brand’s reputation. By proactively seeking out and fixing vulnerabilities, your business can demonstrate commitment to security.
To ensure you get the most out of a web application security assessment. Please take a look at our handy guide (How to plan Web Application Penetration Testing)

The security of a web application is very critical for your organisation or business. A web application penetration service tests the vulnerabilities in the architecture and configuration of the app. To prevent data exposure and unauthorised access, you have to stay prepared with security.
Vulnerabilities in the web app are different from common network vulnerabilities. A web app interacts with many users regularly, which is why it is an easy target for malicious attackers. With our foolproof services, your business will be secured from every cyber threat, and you can run web applications smoothly.
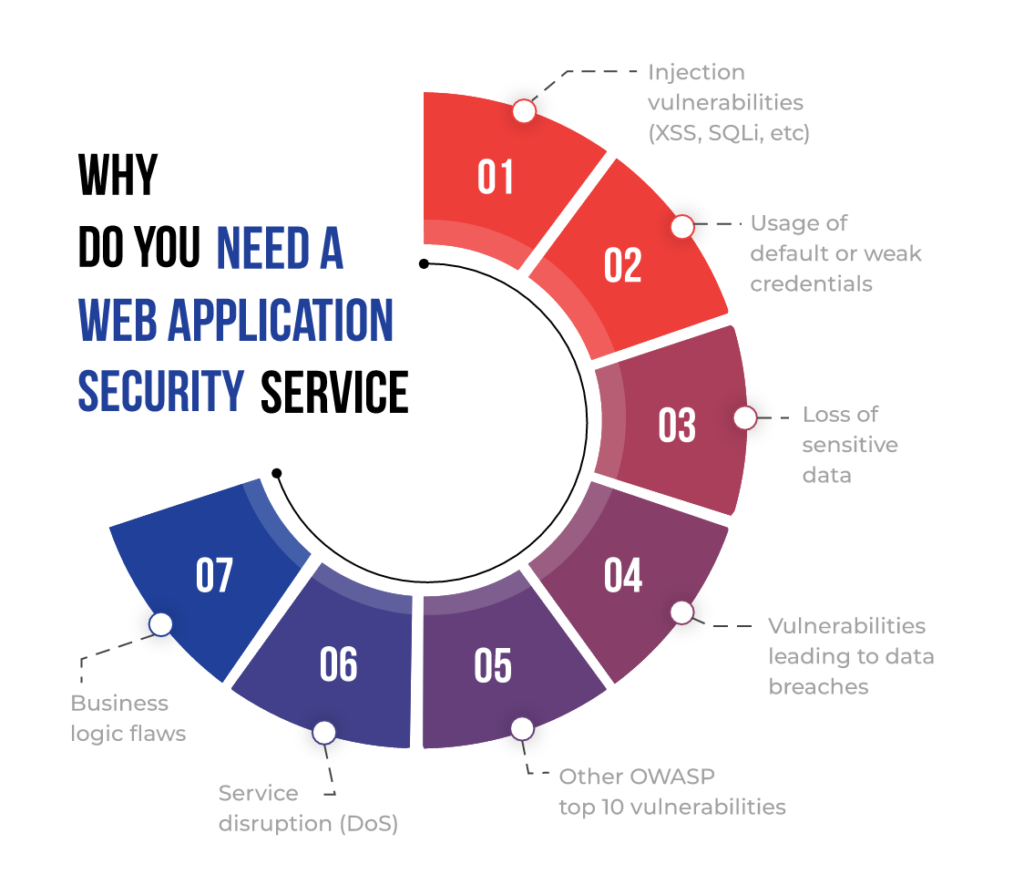
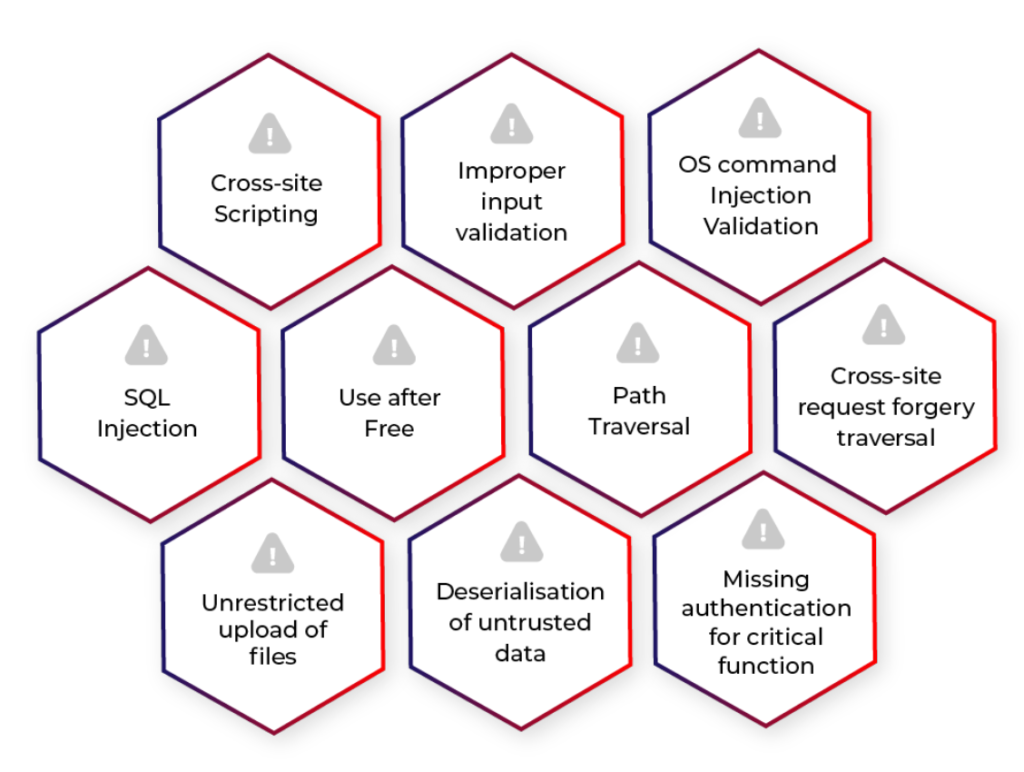
TOP 10 MOST COMMON WEB APPLICATION VULNERABILITIES
In today’s world, a web application might be overwhelmed by a wide range of challenges. Web Applications linger with common security misconfigurations and vulnerabilities. Several of the top attacks employed by attackers can cause significant harm to an individual application or the entire organisation using these vulnerabilities. Knowing the assaults that make an application vulnerable, as well as the probable results of an attack, allows your company to resolve problems in advance and effectively test for them.
What are the benefits of web penetration testing?
Web app penetration testing provides a proactive approach to assess web applications and uncover vulnerabilities that could lead to unauthorised access and data exposure. Pen testing can be used to assess the architecture, design, configuration and/or implementation of apps.
A web app pen test will look for critical risks in apps developed in-house or those from third party vendors, including injection flaws, authentication weaknesses, security misconfigurations and flaws in application logic.
Web app penetration testing enables companies to achieve key outcomes to enhance the overall security of their application. These include improving access control, developing strong authentication and session management controls, ensuring compliance and checking the configuration of firewalls.

Process for web app pentesting

A web app penetration test includes key steps that are completed in a cyclic pattern until no more vulnerabilities are found. The process focuses on the environment and the setup process, aiming to replicate the techniques used by attackers. Following the scoping phase, the testing process begins with collecting information about the web app, mapping the network it is hosted by and investigating any potential points of attack. An extensive threat modelling exercise is conducted prior to attack execution, and the test will conclude with a custom report, listing vulnerabilities by severity and ease of execution, and providing prioritised remediation guidance.